The Scenario
Having touched down in Johannesburg, I am greeted by revision b.04 of the Lockitall LockIT Pro; coupled with an HSM-1 module, the manual states this version of the firmware "rejects passwords which are too long". Somehow I don't have high hopes for their efforts - but that's not important now, let's jump in.
Understanding The Code
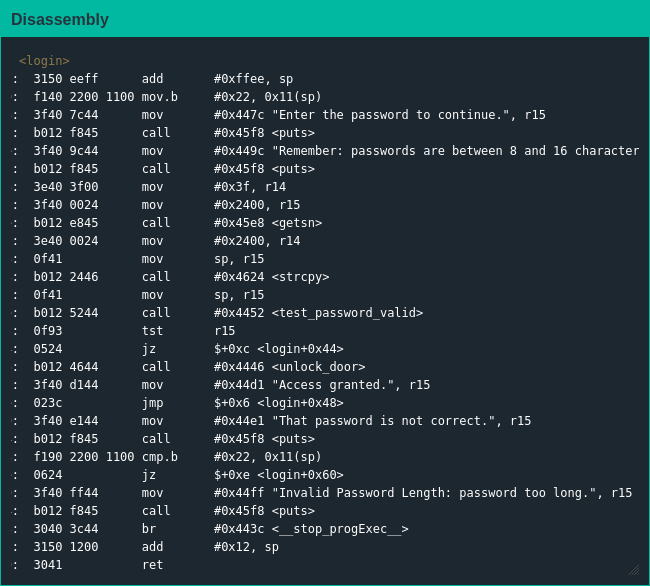
Once again the important code is in the login() function, and given the fact that there is a standalone unlock_door() function it's likely I'll have to do something like in Montevideo to move forward. Unfortunately my first thought to reuse my Montevideo exploit was unsuccessful, with the lock informing me the password I entered was too long - looks like the developers did something.
Exploiting The Code
Then I took a closer look at the assembly and realized the added protection was a stack canary with a constant value. When I used my exploit from Montevideo I overwrote the canary, but I did so with a dummy value, so I could include the canary value into my exploit without much trouble.
With another stack of Yombinator bonds in my possession, I grabbed my surfboard and stack of Prop 65 warning stickers as I set off for sunny southern California.