The Scenario
Having touched down in Johannesburg, I am greeted by revision b.04 of the Lockitall LockIT Pro; coupled with an HSM-1 module, the manual states this version of the firmware "rejects passwords which are too long". Somehow I don't have high hopes for their efforts - but that's not important now, let's jump in.
Understanding The Code
The main functionality is again in login(), and boy is there a lot of it. unlock_door() still exists so the first plan of attack is to figure out what pointer to overwrite to jump there like in Joburg.
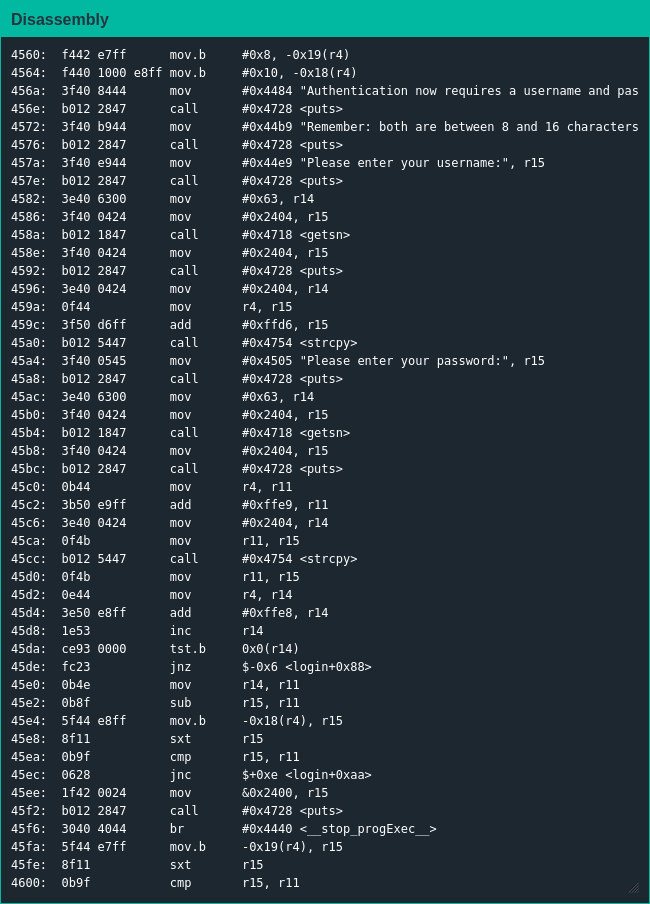
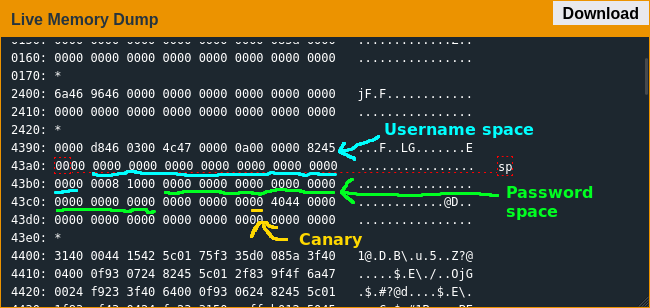
Unlike in previous locales this lock requires a username and password; after strcpy()-ing them into location the lock checks the length of the password against the minimum and maximum lengths written into the firmware. If the password length checks out both the username and password are sent to the HSM, which will write a flag at 0x43a0 to trigger the unlock if the values are correct; finally the firmware checks for a stack canary at 0x43c6 before returning.
Exploiting The Code
My first attempt didn't go so great - since the username length isn't checked it's easy enough to overwrite the min/max password lengths, but reaching the return pointer means writing past the stack canary and including the canary null byte will cause strcpy() to return before overwriting the pointer. Thankfully it didn't take that long to discover the winning strategy of using a long-ass username to overwrite the pointer and the null byte at the end of a shorter username to recreate the canary.
No rest for the wicked though - as soon as this job was finished I had to get wheels up to Indonesia.