Reykjavik was the first challenge that was a stumper for a decent amount of time, so I was looking forward to see how things could get more interesting as I touch down in our neighbor to the north.
The Scenario
The manual for this exercise informed me I was up against hardware version C software revision 1, which has moved the unlocking function from the firmware to the attached LockIT Pro HSM-2. Of course, that won't stop a determined hacker like me so I dove in and got to work.
Understanding The Code
Like in previous challenges main() is a stub function that calls login(), which informs the user about "correct" password lengths before collecting the user's password and calling conditional_unlock_door(). conditional_unlock_door() is a boring function as well, basically just preparing for communications with the HSM to unlock when given the correct password.
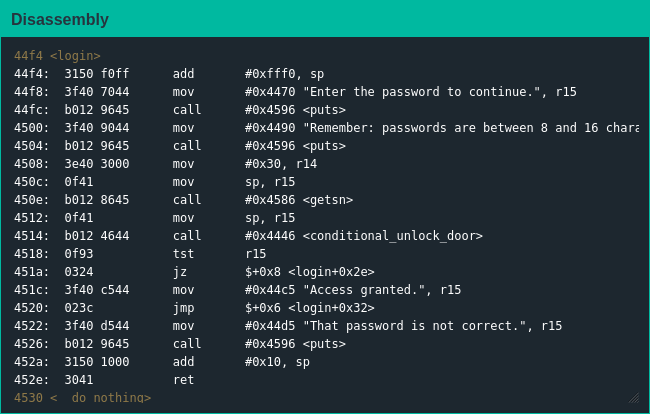
Exploiting The Code
Pretty much immediately I realized this was a variant on what I had done in Cusco, the difference being I would have to write the shellcode to trigger the lock release myself - not a problem, as reviewing earlier challenges let me know all I had to do was push 0x7F onto the stack and call the interrupt handler to get my hands on those sweet sweet Yombinator bonds. The provided assembler turned my assembly into object code, and the rest was history.