After my first Real Hacker Moment(TM) in Cusco, I was excited to see what Iceland had in store.
The Scenario
The manual for this exercise informed me I was up against hardware version A and software revision 2 or 3. There was no HSM I'd have to consider here (perhaps they don't work so far north), but this firmware did have "military-grade on-device encryption"[1]. Usually when people say things like that it makes hacking them easier, but until I jumped in there was no way to know. [2]
Understanding The Code
This challenge began on a markedly different note - no password checking function, no door opening function; main() was a stub once again but it only had a call to enc() before jumping to a location that isn't even considered code:
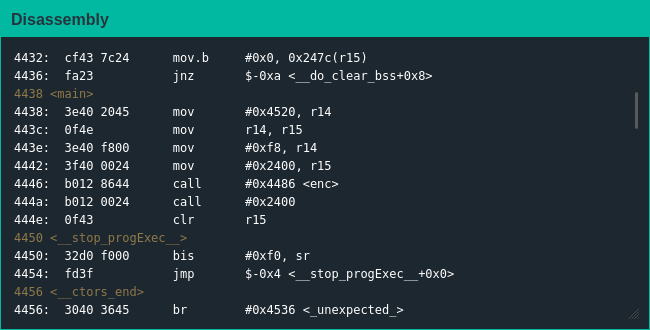
Another weird thing was that enc() didn't seem to just decrypt data, from the expansion of what was around 0x2400 it seemed to almost decompress data as well:
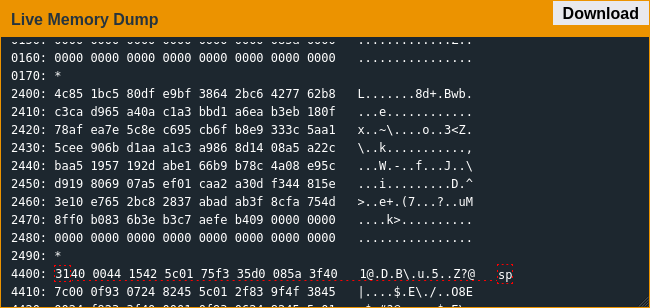
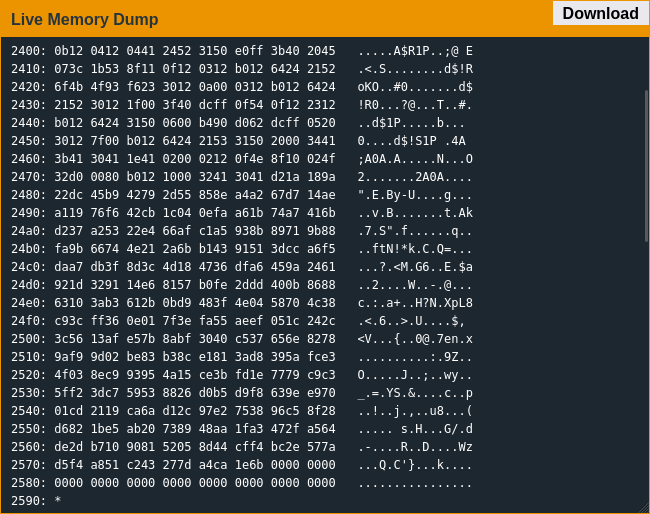
Browsing the rest of memory I saw a string "ThisIsSecureRight?" which was unfortunately not the password; I think it's the decryption key but didn't look into it much since I figured the encryption was a red herring. After control jumped to the middle of nowhere the debugger wasn't much help, so I dumped the memory and dropped the section around 0x2400 into the provided disassembler to get a better look at the code.
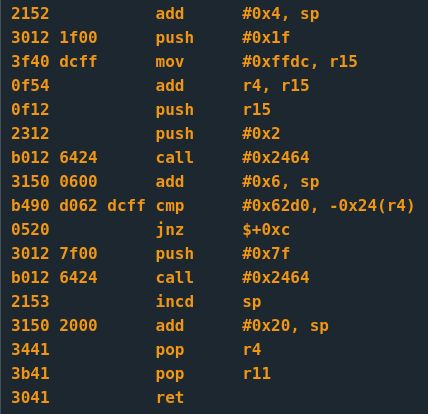
After comparing the instruction patterns in the formerly-encrypted code to those from previous challenges, I managed to determine 0x2400-0x242f prints "what's the password?" to the console, 0x2430-0x2443 gets the password from the user and 0x2464-0x247a is the interrupt handler.
My original thought was this challenge was the same as the last, modulo the crypto aspect, but reading the code a bit more I realized it was similar to an earlier challenge where I had to get a sentinel value in a specific location to trigger the unlock.
Exploiting The Code
After spending half an hour trying to figure out how to access the location I thought I needed to change to no success, I realized I got my hex math wrong and the firmware was looking for the sentinel value in the password; sending the value in little-endian form got me through, and it was on to the next.
| [1] | I didn't figure out what encryption algorithm was in use here, but XOR could be considered "military-grade", and would make sense that rando developers might use it. |
| [2] | An aside: the manual ends with "We apologize for making it too easy for the password to be recovered on prior versions. The engineers responsible have been sacked." Don't threaten me with a good time, Lockitall. |