Jim Wang said it best - "Your email address is the center of your digital life". From shopping to social media, cordcutting to crowdfunding, Allstate to OnlyFans - the modern internet collapses without a platform-independent communication hub.
Since email is of such critical importance, it is then fundamental that that we never lose possession of our email accounts lest we fall to ruin - we have put our digital eggs in one basket, now as Andrew Carnegie once said we must watch that basket.
There are hundreds of commercial email providers on the internet - many boasting about their commitment to their customers' privacy and security - but marketing copy doesn't amount to much when the Ministry of State Security starts poking around, so how is the average netizen supposed to differentiate between who is and isn't full of hot air?
I discovered the difficulty of answering this question while searching for a new email provider last year. After reading one too many articles on my Android phone about the tricks Google uses to access user data, I was fed up. "I cannot remain in this ecosystem" I said to myself, switching from the Chrome app to the Gmail app to tell my local group of infosec nerds more information we kinda knew already.
Switching to Firefox was easy and migrating to iOS was also painless, but email wasn't so simple. Finding a new host for my most precious digital asset required weeks of research. While conducting my research I realized the most important category for measuring security is operational competence: the maturity of their processes, the quality of their infrastructure, et cetera; but finding publically available information on operational competence is nigh-impossible - it's not like companies will brag about their 10-year-old servers that have never seen a spectre update.
This realization was demoralizing until I stopped thinking like a computer scientist and started thinking like an actual scientist, at which point the path forward was obvious - if I can't directly measure operational competence, I'll just have to measure what's most likely affected by operational competence and hope for the best.
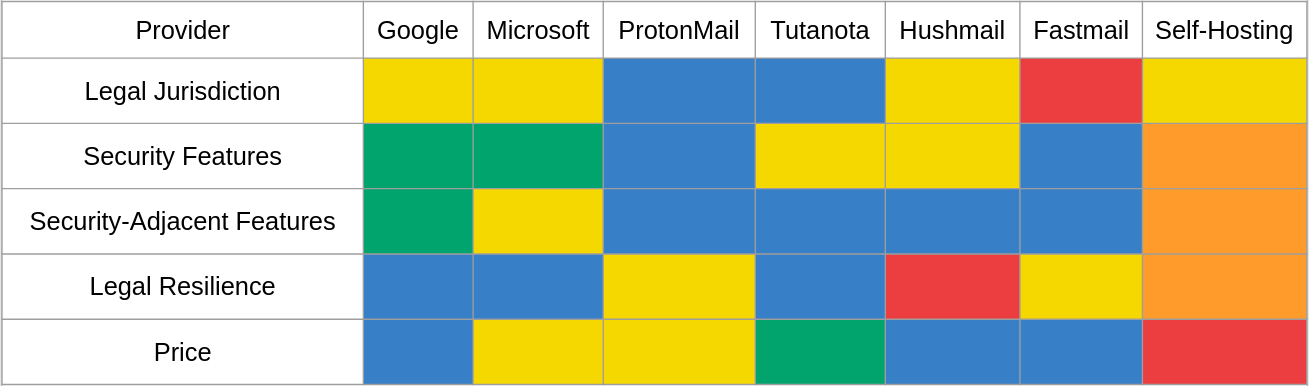
In the end I settled on four categories I believe cover most security-related concerns, and price. To normalize the comparison between providers I decided to use the Chromeland Security Advisory System. I limited my comparison to the largest providers and the most notable privacy-focused providers, with a bone thrown in for the masochists who self-host their email.
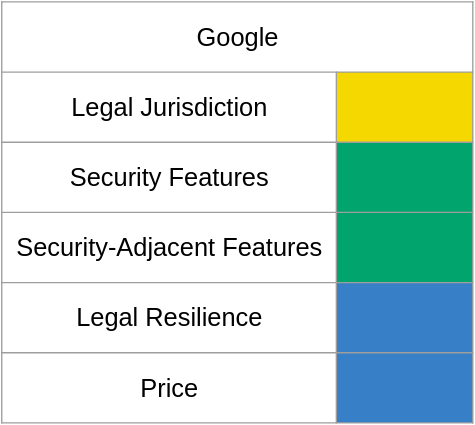
Beginning with Google, the first category is legal jurisdiction, which covers intelligence sharing agreements and the laws of the country or region where data would be stored - and while I did make an effort to consider other people's situations, my analyses in this category will be from the viewpoint of a US citizen residing in the US; YMMV. Google offers email hosting as part of their cloud services product which has changed its name so many times I'll just call it Google Apps. Google gives customers the option to store their data either entirely in the US, entirely in the EU, or anywhere Google chooses. Unsurprisingly data stored in the US can be retrieved through normal means such as orders from secret courts, but with the passage of the CLOUD act foreign governments are now able to demand data from US companies with court orders that haven't been naturalized using an mlat. As I am a US citizen residing in the US the act states foreign govenments should not be able to obtain my data through a CLOUD act request, but that's a pinky-swear more than anything. Looking internationally, like any respectable tax-dodging multinational corporation Google's EU headquarters is in Ireland and Trish laws may come into play, but Google has datacenters throughout the EU and you should generally expect the GDPR to apply to data stored in the EU, with an asterisk for assorted CLOUD act shenanigans. I want to say storing data in the US is no worse than any other "privacy-respecting" country, but I don't believe I can so long as the CLOUD act is in force.
Next is security-related features, which covers things that we generally consider such - 2FA, decent spam/phishing detection and a sufficently robust account recovery workflow. To nobody's surprise, Google has a strong showing with support for TOTP- and U2F-based 2FA. the paranoid among US may appreciate the advanced protection program, but since successfully contacting Google support is np-complete, the basic account recovery flow is likely sufficient for most - if social engineers can't get customer support on the phone, they can't steal your account from under you. I hear a lot of gripes about Google's spam detection but since I receive a thankfully small amount of email I've never really experienced an issue.
Security-adjacent features is where the categories become a bit more subjective, but I believe these features offer a true benefit to security. Google Apps has native support for a catchall address, a lifesaver when you want to discover who might be reselling your information. Sometimes you need to reply from an address originally considered one-way, requiring the ability to use an alias - Google Apps allows 30 active aliases for each user. Lastly Google Apps includes access to Google's Office replacement - this may be the most controversial "security-related" feature, but I think it's the most important: ransomware is the largest threat to computing today and macro-laden documents are the most common method of ransomware infection, so documents handled in the cloud aren't documents that can spread ransomware on a local network.
Legal resilience is another high-subjectivity category that is my attempt to answer the question "how hard will a provider fight for its users?" This category consists of all the news articles and court documents I could find showing the provider fighting assorted court orders. I couldn't find that many instances of Google fighting court orders but the ones I could find were substantial, so I feel comfortable saying Google won't immediately roll over upon receipt of a subpoena.
Lastly is price, which I don't assign much weight to since most everyone watching this is overpaid. At the time of posting Google charges $6 per user-month for the bottom tier of Google Apps, so for a baseline template of one user as a primary account and one user to hold catchall emails, expect to spend $144 per year. If the standard 2 month discount for annual prepayment is available, the price drops to $120 per year.
Microsoft
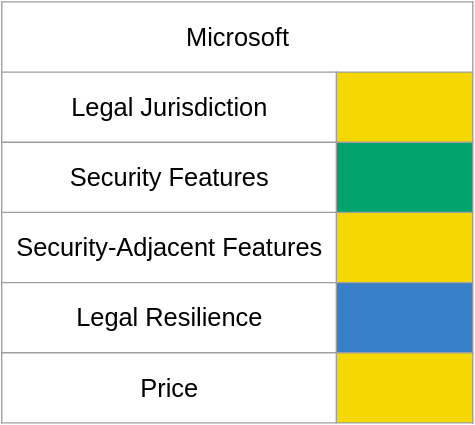
Next is the other 800-pound gorilla of email, Microsoft. MS allows customers to store their data entirely in the US like Google, with similar legal consequences. Internationally, MS also allows customers to store their data either entirely inside Germany or entirely inside France as well as storing it inside the eu generally. france and Germany are both part of the SIGINT Seniors of Europe, more commonly known as 14 eyes, but france is part of the more exclusive group known as 9 eyes. as a member of the eu data stored in Germany is covered by the GDPR, but Germany has its own data protection law conferring additional rights for data owners and additional responsibilities for processors. all of google's jurisdictional issues are present with MS, so they get the same rating.
Microsoft's implementation of security-related features exhibit the differences between an old tech company and an older tech company. MS offers the standard level of spam and phishing detection for their email offerings by default, but depending on your plan for an extra charge customers who store their data outside Germany can enable "Defender for Office 365" which claims to provide enhanced virus scanning for incoming attachments, enhanced phishing detection and link rewriting. 2FA is a mixed bag - while the MS webmail client supports TOTP across all browsers, they decided to not support U2F when using firefox (and for the record, I am assuming U2F dongles work with safari otherwise I have to wonder what they're doing up in Redmond)
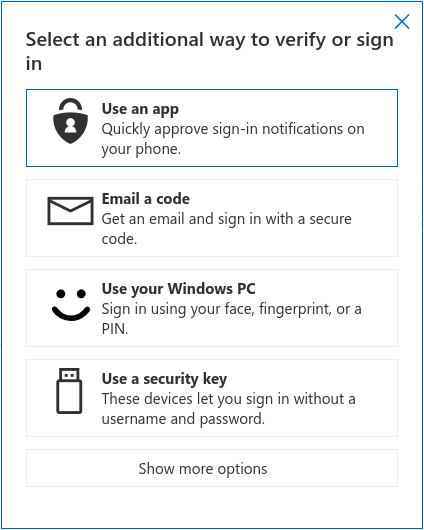
Microsoft's security-adjacent featureset isn't as strong as google's, the most impactful one is access to an online version of Office, but currently the only way to get a catchall address is to use a hack that might not work depending on your plan. MS email accounts get 400 aliases you can reply from, but even though the feature was supposed to have been launched late 2020, it is still not possible to reply from an alias using the outlook web client. Thankfully these are ancillary features, but lack of confidence from the wonkiness of 2FA support is compounded by the lack of native support for a catchall address.
One of the more surprising discoveries from this research is Microsoft's willingness to use its lawyers to fight on their user's behalf in court, successfully quashing multiple gag orders. I wish they'd used those lawyers and lobbyists to shoot down the CLOUD act and make governments go through the MLATs they already had, but I suppose that would have been asking for too much.
Finally there's the question of price, which Microsoft has done its level best to make as difficult to answer as possible. You might have noticed some features were available "depending on your plan" - that's because by my count MS offers no fewer than 13 different products which offer some form of email hosting - even after discarding the obviously unsuitable products that require using godaddy as a registrar or don't support custom domains, there are so many needlessly similar ones left I assume this is some marketing strategy. To be thorough, I asked SwiftOnSecurity about lesser-known plans and was told about a Microsoft 365 E621 tenant which offers Outlook Web Online and an Unmonitored Windows Upgrade license that lets you fully disable telemetry collection, but I couldn't find any information about that plan on the MS website. Pricing correlates with desire to embrace the MS ecosystem, but if email and cloud Office are all you need the top choices are MS365 Business Basic at $120 per year or an Office 365 E1 tenantat $192 per year following the baseline template from before, not counting the extra $2 per user-month for Defender for Office 365.
ProtonMail
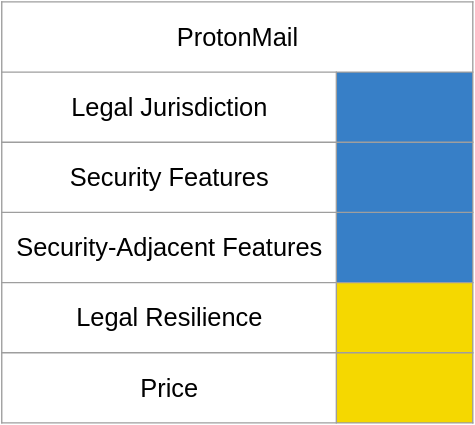
ProtonMail is headquartered in switzerland, using data centers in Switzerland and Germany to store its customers' data. as switzerland is not an eu member, there is no requirement for swiss companies to conform to the GDPR; however article 13 of the Swiss constitution explicitly grants everyone "the right to privacy [...] in relation to their mail and telecommunications" which the swiss federal act on data protection says applies to noncitizens as well. choosing to use a data center in a 14 eyes country when the company takes such a strong stance on privacy seems strange, but as an outsider Germany's additional laws on data privacy on top of the GDPR look strong enough to provide some comfort.
ProtonMail has only basic security features, supporting just TOTP for 2FA alongside spam/phishing detection their subreddit suggests can be hit-or-miss. An additional layer of pin-based encryption is available for data stored in their iOS app.
ProtonMail's security-adjacent featureset is also basic - professional-tier accounts can access catchall addresses and five aliases with the option to purchase more on a yearly basis. The lack of some cloud substitute for office increases vulnerability to ransomware, but this is about the best that can be expected from a company without silicon valley resources.
In terms of legal resilience, despite the number of court orders ProtonMail claims to have challenged in their transparency report, there was no public information supporting such - no news reports covering a legal challenge or court documents available online. It's possible said information is stored somewhere out of sight of search engines, but I find this strange considering I found information on legal challenges for smaller competitors.
ProtonMail's base cost isn't particularly eye-watering, trying to get close to parity with the other providers can get expensive quick. The baseline template costs $16 per user-month or $150 per year, but the professional plan only provides five aliases per user; attempting parity with google's 30 aliases would cost an additional $5 per user-month or $45 per year, costing more than the equivalent MS service with fewer features. This is somewhat disappointing, but as stated earlier this might be the best that can be expected without silicon valley resources.
Tutanota
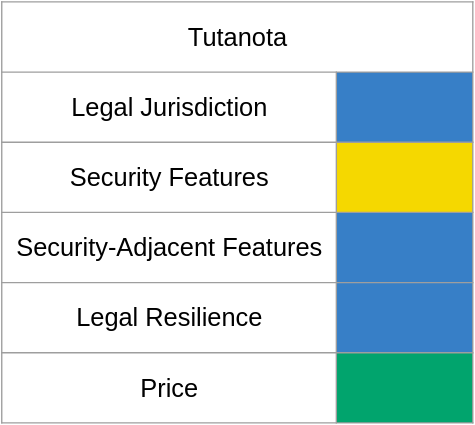
ProtonMail's closest competitor is Tutanota. Tutanota is headquartered in Germany and only uses German data centers, so customer data should be protected by both the GDPR and Germany's data protection act. like with ProtonMail I see some hypocrisy in operating a company with a strong privacy stance in a 14 eyes country, but like I said with ProtonMail Germany's privacy laws should temper most objections.
Like ProtonMail, Tutanota doesn't have much in terms of dedicated security features. Tutanota supports TOTP and U2F for 2FA, but their spam and phishing filters leave much to be desired.
Unsurprisingly, Tutanota has a basic security-adjacent featureset - joining at the premium tier grants five aliases per user and the ability to use catchall accounts, but unlike ProtonMail the additional aliases available for purchase apply across all users in an account. It is currently not possible to set the sender name for individual aliases so if you want to send an email as zero cool instead of dade murphy you have to change your settings so all your email will be sent as zero cool until you change it back. No cloud-based office substitute is available.
In regards to legal resilience, I was surprised to find reports of Tutanota standing up for its users in court and fighting a court order to implement mailbox surveillance despite being such a small company. They lost, but it's the thought that counts here.
Creating a premium-tier account according to the baseline template costs 2 foreigner currency units per month, or roughly 29 freedombucks per year. The closest package to match google's aliases costs as much as the email service, bringing the total to roughly $60 per year.
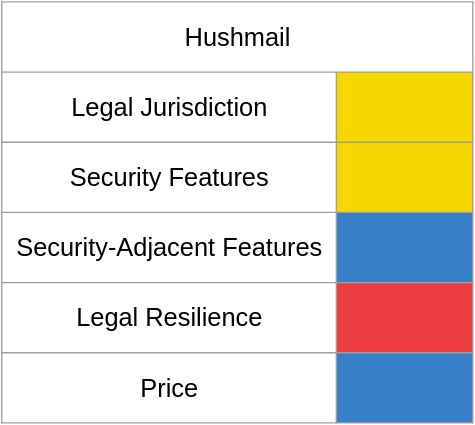
Hushmail
Hushmail is arguably the first privacy-focused email provider, beating gmail to public release by 6 years. Hushmail has the most unusual corporate structure of all the providers in this comparison - the main company, Hush Communications, is incorporated in Delaware with its headquarters in Canada, but everyone's data is stored in Canadian data centers and managed by Hush Communications Canada, a Canadian subsidiary. HCC has to conform to Canada's GDPR equivalent and, assuming it's based in Vancouver alongside Hush Communications, will also have to comply with British Columbia's data privacy law. Spinning operations into a subsidiary looks strange today, but between compressing data before encryption and the resurgence of zoot suits I'm willing to chalk that up to 90s weirdness. Hushmail claims not to be subject to US court orders - perhaps being headquartered in Canada does void US jurisdiction, but absent seeing some case law I don't believe this theory and consider it a US provider.
Hushmail's security-related feature set matches other smaller providers with support for only TOTP codes for 2FA. that said, when 2FA is enabled Hushmail automatically generates an app password for connecting to pop/imap without going through 2FA and somehow that app password includes your normal user password. there are potential ways to do this that don't require the normal user password be stored in plaintext, but their failure to explain how this system works concerns me.
Hushmail's security-adjacent features are somewhat better than the other smaller providers. Business tier accounts get "unlimited" aliases using a Hushmail-specific domain, but additionally get a pool of 100 aliases to use for a custom domain. Business accounts also gain the ability to use a catchall alias with their custom domain. The lack of a cloud-based office equivalent is disappointing like with the other smaller players.
How Hushmail responds to court orders is most likely why it isn't the default choice for a privacy-focused email provider. Those with longer memories might remember this story, but to recap: Hushmail divulged the contents of a customer's messages to authorities as the result of a court order, yet at the time the only way to obtain unencrypted messages between Hushmail customers was to obtain a user's passphrase - either through modifying the code to access the webmail client or modifying the java applet used for client-side access. The lack of any straight answer as to what the company did or did not do suggests Hushmail implemented some sort of vulnerability to collect this information, and the stigma has followed them ever since. I haven't found any info about Hushmail fighting any court orders since, so I feel comfortable in saying much hasn't changed in terms of cooperating with authorities.
Hushmail charges $6 per user-month for the business tier plus a $10 account setup fee, but the lack of annual payment options for this tier only is strange. At this price the baseline template would cost $144 per year, in line with other providers.
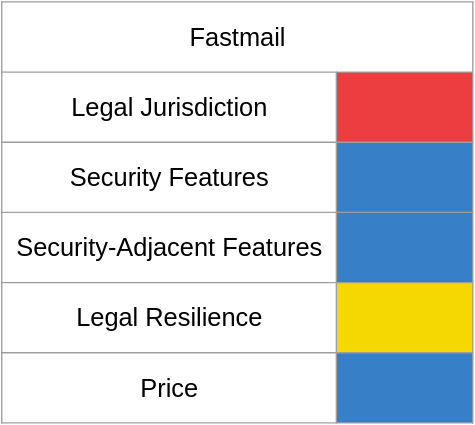
Fastmail
Fastmail is an Australian company but their customers' data is stored in US data centers, likely because inverting packets to run on Australian servers takes too much time. Australia is a member of the UKUSA agreement - colloquially known as five eyes - which raises questions about how private data stored with the company can remain, but recently Australia has taken a huge step in undermining the trust in its tech sector. In 2018 what is known as the AA Bill became law. This law gives large portions of law enforcement carte blanche in what they can order tech companies to do, from building and exercising "interception capabilites" beyond what is proscribed in law to placing secretive government-provided devices on their networks to creating booby-trapped updates - all without requiring a warrant. It's still too soon to speculate on the effect of this law on Australian tech companies - especially since they can only say they've received an order under this law six months after receiving it - but if you didn't like the PATRIOT Act, you should feel even more reticent to store your emails with a company in a country with an even worse implementation of national security letters and a leader who thinks they can regulate hard math.
Fastmail also has a basic security-related featureset, just TOTP/U2F support for 2FA. Their spam and phishing filters were hit-and-miss in the past, but seem to have improved lately.
like the other smaller providers, Fastmail has a basic security-adjacent featureset - the standard tier of accounts can use a catchall account, and every paid account gets a pool of 600 aliases, plus 15 for every user, but the lack of a cloud-based office equivalent is a disappointment.
Fastmail's initial response to the AA Bill's passage was fairly milquetoast, but their main point that they're not a privacy-centric email provider and thus don't engage in those sorts of shenanigans that may result in notices under the aa bill is valid. That said, I couldn't find any evidence of them fighting a court order before or after the AA Bill passed, which makes me think they aren't in the habit of fighting overbroad warrants.
Fastmail is reasonably priced, following the template would cost $10 per user-month or $100 per year, making it one of the cheaper providers in this comparison.
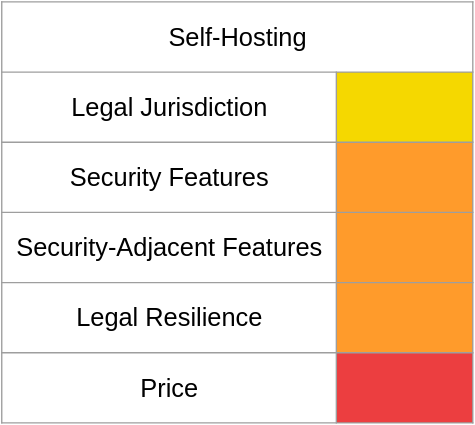
Self-Hosting
And now we arrive at the wild card, self-hosting your email. I originally hadn't planned to make this part of the comparison since everyone who hosts their own email likely does it differently but I figured infosec nerds would be the one group of people where, if I didn't at least mention the concept, no small number would either ask me why I didn't cover it or claim self-hosting doesn't have any of these issues.

If you're self-hosting you get to choose where your emails are stored, but hosting your email server internationally for increased privacy will likely backfire since you will still be where you think your laws suck, so your local law enforcement can target you instead of your server.
Moving on to security-related features - let's be honest, your email setup is a raspberry pi that's maybe just one generation old, running a version of debian you haven't upgraded since you installed it and email software from the third post down on r/selfhosted; if by some chance your setup supports 2FA you don't have it enabled.
In regards to security-adjacent features, self-hosting means you could run anything you want - "cloud" storage, a self-hosted version of office, the world is your oyster. However, unless you decided you wanted all those things when you began self-hosting, laziness likely overtook you so you only have functional-enough email.
on the subject of legal resilience - if a court order arrived at the colo hosting your email server and you're not renting out half the colo, expect them to roll over like a well-trained dog. If for some reason they instead tell the authorities to send it to you, unless you have successful startup exit money you won't be able to fight it when it arrives so you'll roll over anyway.
Determining a price for self-hosting your own email is tricky, because if your time is in any way valuable you've already spent too much and if it isn't the rest of the process will suck you dry anyway. Assuming you only spend about one hour per year maintaining your email server - a big assumption - you're spending more than MS would charge if your time is worth $200 per hour; even if your time's worth only half that you're within spitting distance of most other providers in this review. Even with writing your time off as a learning experience you'll still have to pay the costs of running a computer somewhere, either your own in a colo or someone else's in their data center. You could stick your email server on the best special lowendbox has, but does that really sound like the best idea for privacy or security? The cheapest dedicated servers are $40 per month, so after six months you've still spent more than MS would have charged to handle your email for a whole year.
In Conclusion
Now that the weeks of research have been compiled into a technicolor table, what can be said about the state of email security? To recap, operational competence is supposedly the best indicator of email providers' ability to protect their users from threats on the internet; but since there is so little direct intelligence on the internet about it, this talk attempted to compensate by using more public aspects of a providers' service that hopefully correlate. So was this talk successful in its goals? I don't think so - Microsoft hasn't figured out how to make wildcard aliases work in their 24 years of running an email provider but I still have more faith in them protecting me from a B-tier threat than Tutanota. So what does this mean? aside from the fact that I should stop pretending to be a scientist on the internet, I believe this shows the signals of high operational competence are more fundamental than features providers can stick in checkboxes for comparisons. At this point, I think the least worst signal for determining operational competence might be the size of a dedicated security team - not the conclusion I wanted, but it's the one I can't shake. For now, the big G still has my email.