My jaunt to New Orleans was easy enough, but as I said at the time things will only get harder and I was in the mood for a challenge when I made my way down under.
The Scenario
Upon opening the exercise I am once again presented with the manual for the Lockitall LockIT Pro, only this one is for software revision 2 as "the prior version of the lock was bypassable without knowing the password. We have fixed this and removed the password from memory." Otherwise I'm still targeting hardware version A with no HSM, so I can jump right into the firmware.
Understanding The Code
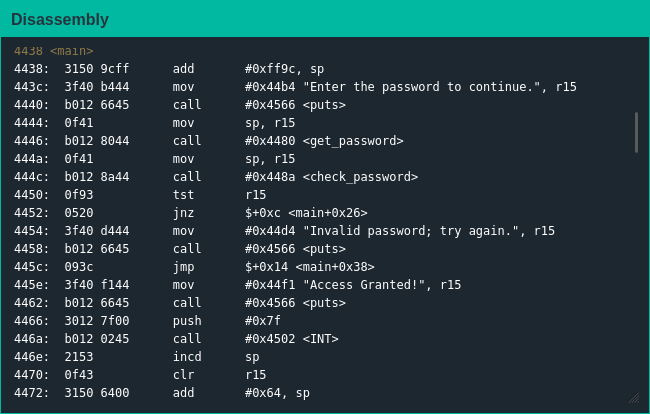
As always, I started by looking at main() for any ideas on how to progress; nothing popped out as obviously as the create_password() function from the last challenge, so I decided to take a look at what secrets the check_password() function holds.
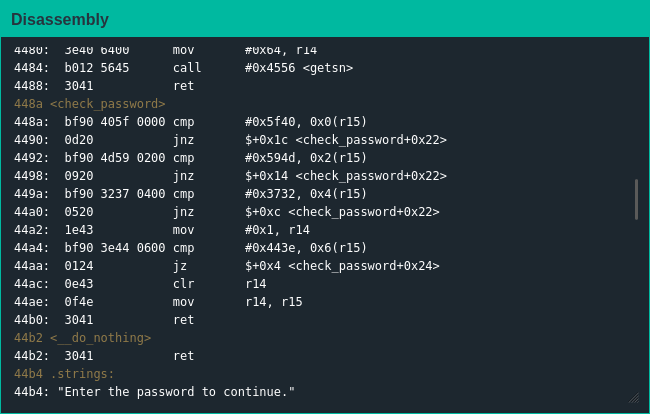
Exploiting The Code
Given that r15 is a pointer to the user-provided password I would guess the static values are the bytes of the password so an attack similar to the last challenge should work again, but since the MSP-430 is little-endian I figured I'd need to swap each two-bit pairing when extracting the password.
This assumption was correct [1], and without much effort I extracted the password and moved on to the next challenge.
| [1] | Side note - even when split into two-byte chunks in the data section the password is still stored in memory; the fact that the Lockitall developers "fixed" the bug by making a barely-different, ultimately-useless change felt fare more real than they likely meant it to. |